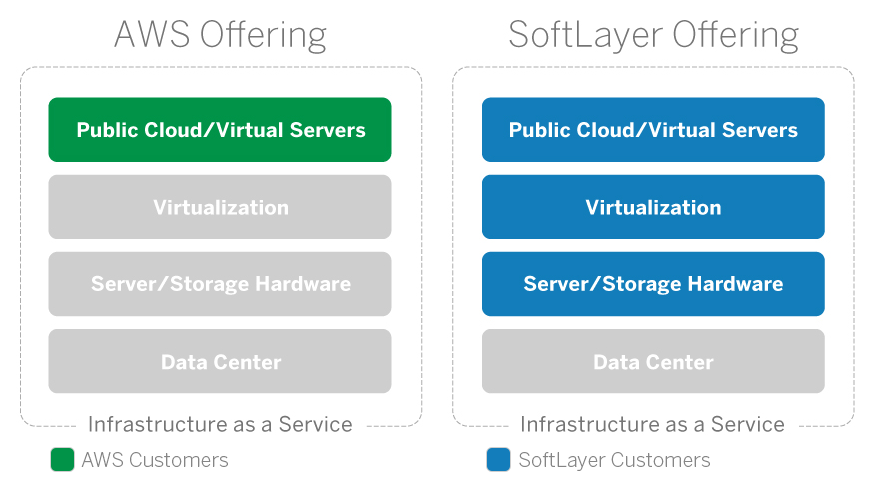
SoftLayer and AWS: What’s the Difference?
People often compare SoftLayer with Amazon Web Services (AWS).
It’s easy to understand why. We’ve both built scalable infrastructure platforms to provide cloud resources to the same broad range of customers—from individual entrepreneurs to the world’s largest enterprises.
But while the desire to compare is understandable, the comparison itself isn’t quite apt. The SoftLayer platform is fundamentally different from AWS.
In fact, AWS could be run on SoftLayer. SoftLayer couldn’t be run on AWS.
AWS provisions in the public cloud.
When AWS started letting customers have virtual machines deployed on the infrastructure that AWS had built for their e-commerce business, AWS accelerated the adoption of virtual server hosting within the existing world of Web hosting.In an AWS cloud environment, customers order the computing and storage resources they need, and AWS deploys those resources on demand. The mechanics of that deployment are important to note, though.
AWS has data centers full of physical servers that are integrated with each other in a massive public cloud environment. These servers are managed and maintained by AWS, and they collectively make up the available cloud infrastructure in the facility.
AWS installs a virtualization layer (also known as hypervisor) on these physical servers to tie the individual nodes into the environment’s total capacity. When a customer orders a cloud server from AWS, this virtualization layer finds a node with the requested resources available and provisions a server image with the customer’s desired operating system, applications, etc. The entire process is quick and automated, and each customer has complete control over the resources he or she ordered.
That virtualization layer is serving a purpose, and it may seem insignificant, but it highlights a critical difference in their platform and ours:
AWS automates and provisions at the hypervisor level, while SoftLayer automates and provisions at the data center level.
Source: http://blog.softlayer.com/2014/softlayer-and-aws-whats-difference