When you make decisions about extending your infrastructure footprint into the cloud, you do so very intentionally. You hunt down analyst reports, ask peers for recommendations, and seek out quantitative research to compare the seemingly endless array of cloud-based options. But how can you be sure that you’re getting the most relevant information for your business case? Bias exists and definitions matter. So each perspective is really just a single input in the decision-making process.
The best process for evaluating any cloud solution involves four simple steps:
- Understand what you need.
- Understand what you’re buying.
- Understand how you’ll use it.
- Test it yourself.
Understand What You Need
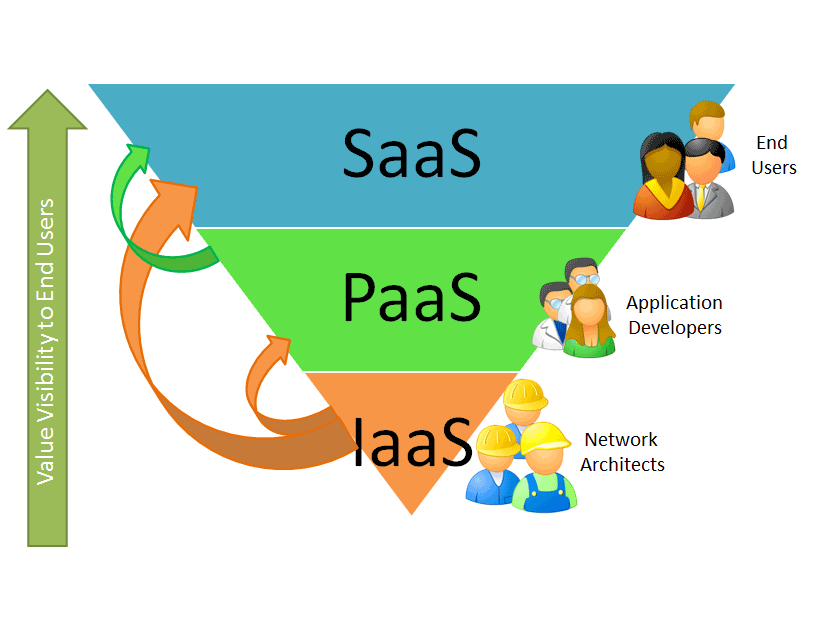
The first step in approaching cloud adoption is to understand the resources your business actually needs. Are you looking to supplement your on-premises infrastructure with raw compute and storage power? Do your developers just need runtimes and turnkey services? Would you prefer infrastructure-abstracted software functionality?
In the past, your answers to those questions may send you to three different cloud providers, but the times are changing. The lines between “Infrastructure as a Service,” “Platform as a Service,” and “Software as a Service” have blurred, and many cloud providers are delivering those offerings side-by-side. While SoftLayer cloud resources would be considered “infrastructure,” SoftLayer is only part of the broader IBM Cloud story.
Within the IBM Cloud portfolio, customers find IaaS, PaaS, and SaaS solutions to meet their unique workload demands. From an infrastructure perspective alone, IBM Cloud offers cloud servers and storage from SoftLayer; containers, databases, deployment, and monitoring tools within Bluemix; and turnkey OpenStack private cloud environments from Blue Box. We are integrating every component of the IBM Cloud portfolio into a seamless user experience so that when a customer needs to add cognitive capabilities or a private cloud or video services to their bare metal server infrastructure, the process is quick and easy.
Any evaluation of SoftLayer as a cloud provider would be shortsighted if it doesn’t take into account the full context of how IBM Cloud is bringing together multiple unique, highly differentiated offerings to provide a dynamic, full-featured portfolio of tools and services in the cloud. And as you determine what you need in the cloud, you should look for a provider that enables the same kind of cross-functional flexibility so that you don’t end up splintering your IT environment across multiple providers.
Source : http://blog.softlayer.com/2016/evaluating-cloud-iaas-gartner-forrester-frost-sullivan